Handshake transcript online. Hacking a WiFi password - decrypting a handshake. Decrypting cap file in WINDOWS
Deciphering the handshake- a difficult process and the reader has probably realized long ago that WPA hacking even with a high-quality handshake and straight hands of the attacker, it looks like roulette. It all depends on the initial complexity of the password. No one can guarantee a favorable outcome, but statistics make us happy and say that at least 20% of WPA networks are successfully hacked, so don’t despair, go ahead!
First you need to prepare a dictionary. WPA dictionary is a regular text file containing one possible password on each line. Considering the password requirements of the WPA standard, possible passwords must have at least 8 and no more than 63 characters and can only consist of numbers, upper and lower case Latin letters and special characters like!@#$%, etc. (by the way, this alphabet is considered quite extensive). The lower limit for the password length is clear, at least 8 characters and a period.
Well, from the top it’s not so simple. It is useless to crack a password of 63 characters using a dictionary, so it is quite reasonable to limit the maximum password length in the dictionary to 14-16 characters. A high-quality dictionary (for which a success rate of 20% is estimated) weighs more than 2 GB and contains about 250 million possible passwords with a length in the specified range of 8-16 characters. What should be included in these combinations of possible passwords to handshake decoding went without a hitch? Firstly, definitely, the entire eight-digit digital range, which, according to statistics, accounts for almost half of all disclosed passwords. After all, various dates fit perfectly into 8 digits, for example 05121988.
And a little more about dictionaries...
A full digital eight-digit number has 10^8 = 100 million combinations, which in itself is quite a lot. In addition, the basic dictionary of the hacker must necessarily include the words most often used as passwords, for example internet, password, qwertyuiop, names, etc., as well as their mutations with popular password extender suffixes (the sole leader in this area is of course the suffix 123). Those. If the diana password is too short to comply with the WPA standard, a resourceful user in most cases will add it to diana123, thereby increasing (in his experienced opinion) the password's secrecy. There are also several dozen such popular suffixes known.
If you're trying to assemble a dictionary yourself (what's the point? Everything was collected before us), you can Google the keywords wpa wordlist and download the ready-made dictionary. Don’t forget about targeting, because it would be quite naive to hope that handshake decoding It will go smoothly if we use the Chinese handshake according to the Russian dictionary and vice versa. You can also look for a suitable one on the Internet, since you can eat them whatever you want.
use crunch to generate various combinations from the basic set
aircrack-ng
Having prepared some kind of high-quality, in our not very experienced opinion, dictionary (for example wordlist.txt), we proceed to password selection, that is, to handshake decoding. Launch aircrack-ng with additional settings:
root@bt:~# aircrack-ng -e
root@bt:~ #aircrack-ng -e |
And here is the result of our labors:

Our password was found in 3 seconds, wow!!!
In the screenshot above, aircrack-ng found the password (and it was the word dictionary) in just 3 seconds. To do this, he tried 3,740 possible passwords at a speed of 1,039 passwords per second. Everything would be fine, but here attentive the reader should be quite tense, because earlier we talked about a dictionary of 250 million possible passwords! And we divide 250*10^6 by 1039 and we get... CHO about 240 thousand seconds, which is 66 hours... Almost three days! This is exactly how long it will take your laptop to process a basic 2GB dictionary (completely, but everyone remembers the “Law of Meanness”). Such irresponsible time intervals are caused by the sluggish speed of calculations, dictated by the high computational complexity of the algorithms embedded in the WPA authentication procedure. What can we say about large dictionaries, for example, a full digital nine-digit character already contains 900 million combinations and will require a couple of weeks of calculations to make sure that (at a minimum) the password is not found)
Such a loser situation could not help but bother the inquisitive minds of our compatriots, and soon a solution was found. For streaming computing, GPUs, that is, video cards, were used. GPU (Graphic Processing Unit) - the heart of your 3D accelerator, has a chip with hundreds (and even thousands) of stream processors, which allows you to distribute multi-million but simple password hashing operations and thereby speed up the decryption process by orders of magnitude. In order not to be unfounded, I will say that the overclocked ATI RADEON HD 5870 is capable of reaching a speed of 100,000 passwords per second! A noticeable difference, isn't it?
decryption of handshake using GPU
Of course, such figures are typical only for top-end ATI RADEON adapters (NVIDIA, with its CUDA technology, is still frankly inferior to ATI in terms of WPA enumeration speed due to the obvious architectural advantages of the latter). But you have to pay for everything, a good video accelerator is expensive, and is usually found only among avid gamers, or otherwise - nerds.
As part of this article for beginners, I probably won’t delve into the jungle of setting up the ATI SDK and pyrit for Linux, I’ll just note that you’ll have to have sex for a long time and with high quality. And there are not so many owners of top-end Radeons with Nvidia, I think they will figure it out quite independently. Well, or Google it)
Paradoxically, Windows is best suited for guessing a WPA password using a GPU, yes, yes, that’s it). The fact is that video adapter drivers play a significant role in this process, the Windows versions of which developers pay much more attention to than drivers for Linux. After all, they focus on the needs of gamers. Do you know many people who like to play on a computer with Linux installed? Two programs can select a WPA password for Windows: the commercial Elcomsoft Wireless Security Auditor and the console utility hashcat-plus. We will consider the use of these programs further, and at the same time compare their characteristics, talk about the pros and cons of both. Let's see at what speed it will happen handshake decoding under equal conditions, on the same system for both programs.
Having the latest working video card drivers in the system is a must. I won’t tell you how to install firewood on the video camera, since you’re here, I’m sure it’s a piece of cake for you.
Decoding the Elcomsoft Wireless Security Auditor handshake
EWSA can be found (and purchased) on the developers’ website - www.elcomsoft.com, just keep in mind that the free trial version, according to rumors, does not show the found password. On the Internet you can find broken versions of different quality, just don’t forget about the remorse that will torment you). Installing and configuring EWSA is elementary, you can immediately select the Russian language in the menu, in the GPU settings, make sure that your GPUs are visible to the program and selected by checkboxes (if the GPUs are not visible in the list, you clearly have a problem with the drivers), and also indicate to the program the paths to your dictionaries in the dictionary settings.

Click “Import data -> Import TCPDUMP file” and select the *.cap file with a handshake (the program will check them and offer to mark those that we want to attack), after which you can safely click “Launch attack -> Dictionary attack”:

Hmm... It could have been more fun))
In this test, EWSA showed a speed of only 135,000 passwords per second, although based on the hardware configuration I expected to see a figure of about four hundred thousand.
Decoding the EWSA handshake
Let's compare the work of EWSA with its truly free competitor - hashcat-plus. Download the full set of hashcat-gui from the author’s website and extract the archive to a convenient place, it’s portable. We launch hashcat-gui32.exe or hashcat-gui64.exe depending on the bitness of Windows and answer the first question which GPU we will use - NVidia (CUDA) or ATI RADEON (the CPU only option obviously will not suit us).
When the main program window loads, go to the oclHashcat-plus tab (or cudaHashcat-plus in the case of NVidia). There is one subtlety here - hashcat does not know how to parse EAPOL handshakes, it does not know how at all and does not know what it is. He requires you to give him WPA hashes “on a silver platter” in his own *.hccap format. You can convert regular *.cap to *.hccap using the patched aircrack-ng utility! The developer of hashcat has made a convenient online converter, just upload your *.cap file with a handshake there and specify the ESSID, if there is a handshake in the file, the *.hccap will be returned ready for attack. Well, if not, then there is no trial).
Let's move on - we indicate to the program our *.hccap file as the Hash file for the attack, add dictionary files to the Word lists window (you can use the arrows to set the desired order of their passage), select WPA/WPA2 as the Hash type and click on Start.
A console window should appear with the launch of the selected version of hashcat-plus and a bunch of parameters, and if everything is in order, the utility will start working. During the calculation process, you can display the current status by pressing the ‘s’ key. You can pause the process by pressing 'p' or interrupt it by pressing 'q'. If hashcat-plus suddenly finds the password, it will definitely show it to you..

The result is 392,000 passwords per second! And this agrees very well with the theoretical expected speed, based on the system configuration and pencil calculations.
This test convincingly shows that hashcat-plus is much more scalable when using multiple GPUs simultaneously. The choice is yours.
- free access
- dictionary size
- supported hash types
- availability of detailed cryptanalysis (for example, using Rainbow tables)
Updated 10/17/2019
- cmd5.ru
cmd5.ru is one of the oldest services for decrypting hashes, existing since 2006. Advantages of the service:- a unique database, unparalleled in volume - 4800 billion records;
- a huge number of supported hash types for brute force;
- possibility of group processing of hashes;
- Availability of a software client to access the service.
In addition to free access to the service, there is an extended paid package of services. Is it worth paying for decryption? Definitely yes, especially in cases where no other service can crack your password, or you are engaged in decrypting hashes on an ongoing basis, especially since the rates are quite affordable. From my own experience, I can say that this is the most effective service, which is why it takes an honorable first place.
hash types:
- md5(md5($pass))
- sha256
- mysql
- mysql5
- md5($pass.$salt);Joomla
- md5($salt.$pass);osCommerce
- md5(md5($pass).$salt);Vbulletin;IceBB;Discuz
- md5(md5($salt).$pass)
- md5($salt.$pass.$salt);TBDev
- md5($salt.md5($pass))
- md5(md5($pass).md5($salt))
- md5(md5($salt).md5($pass));ipb;mybb
- sha1($salt.$pass)
- sha1(lower($username).$pass);SMF
- sha1(upper($username).’:’.upper($pass));ManGOS
- sha1($username.’:’.$pass)
- sha1(salt.pass.’UltimateArena’)
- MD5(Unix);phpBB3;WordPress
- Des(unix)
- mssql
- md5(unicode)
- serv-u
- radmin v2.x
- xsrc.ru
free + paid | 100G | wpa pmkid | dictionary crowdxsrc.ru is an excellent service for selecting WPA handshakes; it is possible to purchase selected passwords from authorized service members with their own hash selection capabilities for a small fee.
- crackstation.net
free | 190G | LM NTLM md2 md4 md5 md5(md5) md5-half sha1 sha1(sha1_bin()) sha224 sha256 sha384 sha512 ripeMD160 whirlpool MySQL 4.1+ | dicThe description of the service states that the database includes all words from Wikipedia, as well as all publicly available dictionaries that the author managed to find on the Internet. The dictionary used by the service is available for download. In addition, there is a twitter bot @plzcrack.
- md5.darkbyte.ru
free | 329M+48G | md5 | dicThe service gives good results, as it uses third-party services in addition to its own local database. Allows you to send an unlimited number of passwords for decryption, there is an API.
- tmto.org
free | 36G | md5 lm ntlm sha1 | rainbow tablesAfter a long period of offline, the TMTO (Time-Memory Trade Off Cracking) project has become available again. The database became even larger, new algorithms appeared, the service remained free, as before. I am pleased with the high decryption speed due to the constant growth of the cluster. You can send an unlimited number of hashes for decryption at one time.
- hashcracking.ru
free & authentic | 3M | md5 mysql mysql5 sha1 | dic rainbow tableshashcracking.ru is still in operation, it allows you to search for mysql and mysql5 passwords, brute force using a mask, and it is possible to search through a dictionary with the salt specified.
- www.md5decrypter.co.uk
free | 8.7G | md5 | dicA good free service with a decent base. You can send 12 md5 hashes for processing at a time. Among the disadvantages, it can be noted that only a dictionary check of the found passwords is used.
This article will be devoted to the method of intercepting wifi network data packets, also called interception (capture) of wifi network handshake packets.
There are many ways to capture these “delicious” data packets. In the current article, the wifi password recovery service will offer you a shell option AirSlax. This software is very convenient for using Wi-Fi network password recovery, intercepting handshake, automatically finding WPS password and much more.
First, let's prepare the tools.
We will need any flash drive, popularly known as a “flash drive,” with a capacity of more than 2GB. Then we download the archive with the program AirSlax by this
After this, you load the contents of the archive into the root of the flash drive (USB Flash)
Go to the boot folder and run the installation program. In our version, this will be Porteus-installer-for-Windows.exe. Then a “black” window will appear and in it we press the spacebar or any key to allow further actions * .
We are waiting for the message Installation finished successfully to appear.

And press any key to close this window.
That's it, the shell image is already loaded onto the flash drive. All that remains is to reboot the computer and select boot mode from a flash drive.
The download selection can usually be done via F12 button on a desktop PC or via Fn+F12 on laptops, the choice can also be made through Bios.
from a flash driveAfter successfully selecting the boot mode, you will see a startup menu on the screen, if you do not select the items ** , then the launch will be carried out automatically.
We wait until the operating system boots.
At the end of the download we will have a desktop on the screen and launch the AirSlax Base shortcut by double clicking. A window for selecting a wireless adapter will appear in front of us:

Select and click OK, the main menu will appear on our screen:

The action plan now is as follows, first click on the item “ Scan air", we have a new dialog box:

Shows the current status of active networks. We are waiting for the active users of the Wi-Fi network we need to appear at the bottom of the table. The key point here will be “ STATION". We see that there are active connections to the desired network from the poppy addresses. We close the window. Click on 2 items “Select network”, indicate the desired MAC address:

click OK
A new window will open with the target we have already selected:
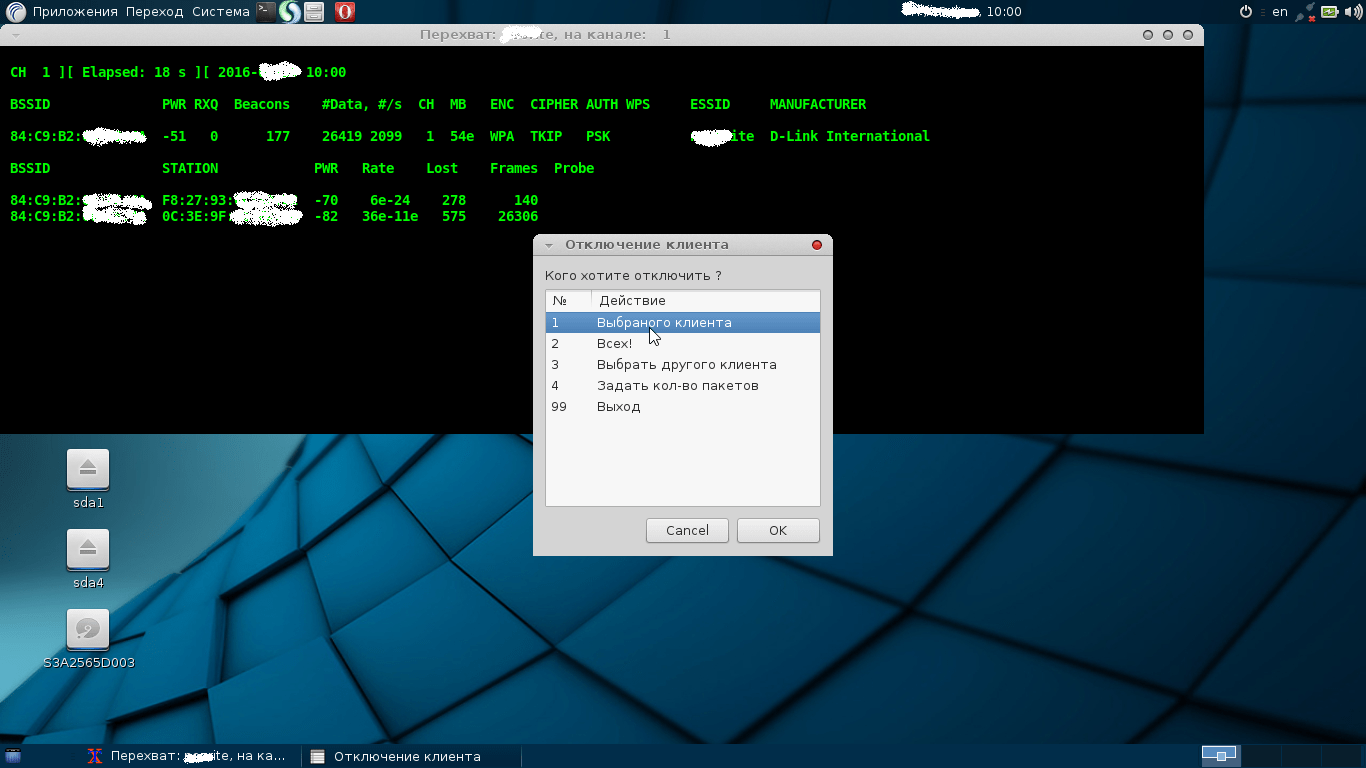
Now we need to catch handshake for finding a password from a wifi network Select item 4 " Disconnect client» and indicate the selected client. In rare cases, you can specify everyone. Now we wait until the device reconnects to the Wi-Fi network we selected. If successful, we will see the text “ WPA handshake»

Close the black capture window and select item 6 in the menu “ Save result". Specify the file name and click OK. Now there will be a folder on the flash drive dump. From the dump folder we take the files “network-name-wifi.cap” or “network-name-wifi.hccap” and upload them in the order on the page
We are waiting for the order to be completed from the service. The end!
*Press to exit X
**Select launch via Graphics mode (MATE)
This article will talk about how to hack a Wi-Fi network with WPA/WPA2 encryption by intercepting a handshake. But first, the theory.
WPA/WPA2 theory
WPA (or WPA v1 as it is sometimes called) typically uses the TKIP encryption algorithm. TKIP was designed to enhance WEP encryption without requiring hardware modifications to work. WPA2 necessarily uses the AES-CCMP encryption algorithm, which is more powerful and secure than TKIP.
WPA and WPA2 allow you to use either EAS-bases authentication (RADIUS Server “Enterprise”) or Pre-Shared Key (PSK) “Personal”-based authentication.
WPA/WPA2 PSK encryptions are vulnerable to dictionary attacks. To carry out this attack, you must obtain 4-way WPA handshake between the wifi client and the access point (AP), as well as a dictionary containing a passphrase.
WPA/WPA2 PSK works like this: it is derived from the pre-session key, which is called Pairwise Transient Key (PTK). PTK, in turn, uses Pre-Shared Key and five other parameters - SSID, Authenticator Nounce (ANounce), Supplicant Nounce (SNounce), Authenticator MAC-address (Access point MAC address) And Suppliant MAC-address (Wi-Fi client MAC address). This key further uses encryption between the access point (AP) and the wifi client.
An attacker who is listening to the broadcast at this moment in time can intercept all five parameters (see the previous paragraph). The only thing that the villain does not own is the Pre-Shared key. Let's find out how the Pre-Shared key is created.
The Pre-Shared key is obtained/created by using the WPA-PSK passphrase that the user submits, along with the SSID. The combination of these two parameters is sent via Password Based Key Derivation Function (PBKDF2), which outputs the 256-bit shared key.
In a normal/typical WPA/WPA2 PSK dictionary attack, the attacker will use a dictionary with a program/tool. The program will output a 256-bit Pre-Shared Key for each passphrase and will use it with the other parameters that were described in creating the PTK. PTK will be used for verification Message Integrity Check (MIC) in one of the handshake packages. If they match, then the passphrase in the dictionary will be correct, otherwise it will be the opposite (incorrect). This is exactly how WPA/WPA2 PSK works.
Practice
Important:Don't forget that you need to choose the right wifi client! To do this, carefully look at the details of the supported chipsets. As a client I use ALFA AWUS036H.
Once the “right” hardware has been purchased/selected, we proceed to setting it up. First, let's run the airmon-ng command to find out what interfaces are available in the system:
A virtual interface has been created mon0, we will work with him.
Now we scan the air using airodump-ng:
$ sudo airodump - ng mon0
Since we are all “good”, we will test everything on our APs. In my case it's TestWireless. Let's switch to it:
$ sudo airodump - ng - w handshaketest - c 1 -- bssid BC : AE : C5 : 71 : D3 : 17 mon0
- -w– name of the dump file
- -c– channel number
- –bssid– MAC address of the access point
We see that a client is connected to the AP. This is what we need, because we know - Handshake interception is possible if and only if a client is connected to the AP.
Now leave the terminal window where it works airodump-ng open. Open a new window in which we write:
$ sudo aireplay - ng - 0 3 - a BC : AE : C5 : 71 : D3 : 17 - c 70 : F1 : A1 : 72 : b4 : 25 mon0
- -0 - deauthentication
- 3 — number of packages
- -a— MAC address of the access point (AP)
- -c— MAC address of the client to which deauthentication is applied
Handshake - in simple terms, a file that contains an encrypted password for a Wi-Fi network.
And here is a list of services that decrypt handshakes for free:
Aircloud-ng.me
- a semi-free service that will run your handshake through 58 dictionaries, the number is certainly impressive, but the ones that don’t often include passwords are Russian-speaking users.
In order to send a file, just specify your email and select the appropriate cap/pcap handshake.
There is still a chance of finding the password on it, but it is close to zero.
wpa-sec.stanev.org
- the service, which contains 18 popular dictionaries, very often helps because
contains quite good dictionaries, for example isider_pro_wpa, the full list of dictionaries can be found on the site itself. It often hangs, unable to withstand the flow of freeloaders, in which case the admin limits the brute force to only 2 dictionaries, but this happens temporarily when the server is freed up and supplies the rest of the dictionaries.
wpa-darkicop.org - It’s also a free service, but for some reason it hasn’t been working lately.
The run goes through the following dictionaries: Rainbow, CoW (1M), Openwall (3M), Insidepro (11M), Offensive security (39M)
From the free ones, I’ll also note a couple of topics of the same name on other forums:
antichat - very often they help out, but what can they help out... they practically live with these handshakes, in the full sense of the word)
Post strictly according to the rules and you will find help. It happens that they run through phones and rare dictionaries that are not in the public domain, in many paid services and they don’t even do that. Probability of finding a pass: 60%
insider about - Also quite an old forum, there is a topic where they help you find a pass, but it is slowly becoming covered with cobwebs.
Paid:
onlinehashcrack.com - To be honest, I used it several times, at first it was free, now only for money, on average 3-4 $ per found password. It is unknown what dictionaries it contains, I tried to find out, contact the site administrator, but to no avail, I never received an answer. Finds only banal dates of birth and English words.
xsrc.ru - I’ll say one thing about it, about 4 months ago I downloaded a handshake from a waffle, whose password is a regular RU phone number, this service did not find this password, it often finds simple 8-digit passes, dates of birth, the list of dictionaries is not known to me.
cloudcracker.com- as stated in the advertisement, it runs 300,000,000 words in 20 minutes, there are 3 dictionaries to choose from (english, 2wire, phone numbers) where you can select the number of words that will be brute. The dictionaries are tailored more to us-en countries; the price for decryption can reach up to $136, depending on how many lines of words you choose, and you have to pay regardless of whether the service finds the password or not.
gpuhash.me - Quite a high-quality service, contains many different dictionaries, passwords that are actually often set, focused on ru and us passwords. There is a free run through the basic dictionary.
airslax.com- service from the author of the airslax distribution, the price for 1 found password is 5usd. Checks handshake against standard dictionaries of numbers, mobile phones of Ukraine and Russia.
pwaudit.com -It looks pretty good and is very convenient, you can view detailed statistics of the brute, by the way it supports a large number of types of hashes. Currently, the database contains 9TB of rainbow tables and more than 15GB of “clean” passwords
What else to read
THE LAST NOTES
- Vegan pumpkin stuffed with rice and baked whole in the oven
- Teleportation and time travel
- Notification of changes in the terms of the employment contract and transition to an effective contract Notification of the employee about the introduction of an effective contract
- Liquid buckwheat porridge - benefits in every spoon
- Step-by-step photo recipe for freezing vegetables for borscht for the winter at home Freezing borscht for the winter with beets
